Crypto Malware
Crypto malware, short for cryptocurrency malware, represents a subset of malicious software specifically crafted to target, exploit, and compromise crypto-based activities.
Cryptocurrencies have heralded a new era of financial autonomy, unhinged from centralized banks and opaque financial systems. But as with every innovation, there’s a double-edged sword.
The decentralized nature of cryptocurrencies, as empowering as it is, has also paved the way for a series of challenges, notably in the form of crypto malware attacks and the exploits of malicious actors.
This decentralization, while laudable for its democratization of financial systems, unfortunately lacks a centralized authority to oversee and ward off security threats. As a result, the responsibility to protect one’s assets in this space falls squarely on individual users. This wouldn’t be a significant issue if the vast majority of crypto users were well-versed in digital security. However, reality paints a different picture.
A large portion of the crypto community remains unaware or ill-equipped to handle the intricate web of security threats in this domain. This lack of knowledge, combined with the lucrative allure of cryptocurrencies, creates a perfect storm – a utopia for cybercriminals. They find it easy to prey on ignorance, exploiting vulnerabilities and reaping rewards from those unaware.
One such menacing threat is “crypto malware,” or “crypto mining malware.”
In this guide, we will delve deep into what is crypto malware, how to detect crypto mining malware.
Table of contents
- What is Crypto Malware (a.k.a. Crypto Mining Malware)?
- The Deal with Crypto Mining Malware
- How to Detect Crypto Mining Malware?
- Types of Crypto Malware
- Crypto Malware Examples
- Useful links
- How to Remove Crypto Mining Malware
- How to Protect Against Crypto Malware
- Cryptomalware Was Inevitable. Stay Safe with Paybis.
What is Crypto Malware (a.k.a. Crypto Mining Malware)?
Crypto malware, short for cryptocurrency malware, represents a subset of malicious software specifically crafted to target, exploit, and compromise crypto-based activities.
Whether it’s stealing access to your crypto wallet, illicitly mining coins using your computer’s resources or holding your digital assets ransom, crypto malware has various detrimental forms.
To further illustrate, consider “cryptojacking” – a term that often goes hand in hand with crypto malware. Cryptojacking refers to the unauthorized use of a user’s computer resources to mine cryptocurrencies.
Typically, attackers embed malicious code into websites or software, and when an unsuspecting user visits such a site or downloads the compromised software, the mining script starts running in the background, using the victim’s resources without their consent or knowledge.
Now, you know the crypto malware definition. But what makes it so worrisome?
The Deal with Crypto Mining Malware
Imagine, for a moment, you own a beautiful home. One day, unbeknownst to you, a stranger finds a hidden way into your home, and they decide to stay.
They utilize your living space, eat from your kitchen, take long showers, and even host parties, all while you’re away. Every utility they use increases your bills. The wear and tear from their activities cause damages that you’ll eventually need to repair. And yet, when you come back home every evening, everything seems to be in place: no signs of forced entry, no clues, and thus, you remain oblivious.
This surreptitious occupation of your personal space, and the damages and bills you’re unknowingly burdened with, are akin to the silent threat of crypto malware.
Your computer, much like your home, is personal and holds valuable assets. When crypto malware sneaks in, it covertly uses your system’s resources, mines cryptocurrencies, or even steals your digital assets, all while you might be just browsing the internet or working on a document. And, as with the stranger in your home, the consequences are costly – not just in monetary terms, but also the wear and tear on your device and the potential loss of privacy and data.
The proliferation of crypto attack emphasizes the necessity for digital asset holders, particularly those dealing with cryptocurrencies, to remain vigilant and informed.
How to Detect Crypto Mining Malware?
Crypto mining malware, often sneaking in unnoticed, can exploit your device’s resources to mine cryptocurrency for malicious actors. Given its covert nature, it’s essential to know the signs and tools to detect it.
The table below explains how to check for crypto mining malware (note that the table is not exhaustive).
Symptom/Indicator |
Action/Resolution |
| Unusual CPU and GPU usage | Check Task Manager (Windows) or Activity Monitor (macOS) for high-consuming unfamiliar processes. |
| Overheating | Use tools like HWMonitor or SpeedFan to monitor device temperature. |
| Increased fan activity | Listen for unexpected fan noises; cross-check with the system’s performance monitor. |
| Performance issues on web browsers | Install browser extensions like No Coin or MinerBlock to block potential mining scripts. |
| Websites running unfamiliar/irrelevant scripts | Utilize web developer tools in browsers to inspect site codes for mining scripts like Coinhive. |
| Increased Network Activity | Use tools such as Wireshark to monitor and analyze suspicious network traffic or connections. |
| Higher electricity bills | Review unexplained spikes in electricity usage and consider running a full system scan if other indicators align. |
| Unexpected system crashes | Investigate reasons for sudden system crashes. Perform comprehensive malware scans using trusted antivirus software. |
| Unusual file patterns | Crypto malware may create or modify files in system directories. Regularly scanning your system for unfamiliar files or folders, especially in system directories, can help detect malware presence. |
Types of Crypto Malware

As with many malicious software types, crypto-malware isn’t a monolithic entity. Instead, it presents itself in various forms, each tailored for specific malicious intents related to digital currencies. Here’s an exploration of its different avatars:
Crypto Mining Malware
Among the most common types of crypto malware, crypto miners are designed to exploit a victim’s computer resources (like CPU and GPU power) to mine cryptocurrency.
By harnessing these resources, cybercriminals can mine digital currencies without investing in the necessary infrastructure themselves, essentially getting monetary rewards at the victim’s expense.
The malicious software often runs secretly in the background, slowing down the victim’s computer and potentially causing long-term hardware damage due to overuse.
Crypto Ransomware
A formidable adversary, crypto ransomware is malware that encrypts a victim’s files, rendering them inaccessible.
The attacker then demands a ransom, usually in cryptocurrency due to its anonymous nature, in exchange for the decryption key.
One of the most infamous examples of this is the “Cryptolocker” attack, which resulted in countless individuals and businesses losing essential data or paying a hefty ransom.
Crypto Stealing Trojans
These malicious programs masquerade as legitimate software or hide within them.
Once installed on a victim’s device, they seek out and pilfer cryptocurrency wallet details, enabling the attacker to steal the victim’s funds.
Clipboard Hijackers
In a more stealthy approach, clipboard hijackers monitor the clipboard of a user’s device for cryptocurrency addresses (which are usually long and get copied and pasted).
Once detected, they swap the copied address with the attacker’s address.
Unwary victims may end up transferring their digital assets to the attacker’s wallet without realizing the switch.
Phishing Scams Targeting Crypto Users
Not malware in the traditional sense, but still a significant threat in the crypto sphere.
Cybercriminals trick users into entering their crypto wallet details on fake websites that appear genuine.
Once the details are entered, attackers gain full access to the victim’s wallet and funds.
Crypto Malware Examples
The ever-evolving world of cyber threats has seen multiple instances where crypto malware made headlines, not just for their innovation but also for the sheer magnitude of damage they inflicted. Let’s delve into some notable examples to truly understand the extent of this threat:
WannaCry Ransomware Attack
Perhaps one of the most infamous crypto malware examples, the WannaCry ransomware spread across 150 countries in 2017, affecting over 230,000 computers.
It encrypted user data and demanded Bitcoin ransom for its release.
Organizations worldwide, including major hospitals, were paralyzed, leading to estimated damages ranging from hundreds of millions to billions of dollars.
Coinhive Cryptominers
Coinhive was a legitimate service that offered website owners an alternative to ad revenue. By embedding the Coinhive script, website visitors’ computational power would be used to mine Monero, a privacy-focused cryptocurrency.
However, malicious actors quickly adopted this tool, injecting the script into various websites without the knowledge or consent of the site owners or visitors.
This unauthorized cryptojacking became so widespread that Coinhive eventually shut down its operations.
The Cryptolocker Attack
As previously mentioned, in the context of ransomware, Cryptolocker is another devastating example.
Upon infecting a computer, it encrypted the user’s files and demanded a Bitcoin ransom for the decryption key.
Many victims were left with the grim choice of paying the ransom or losing their data permanently.
Bad Rabbit Ransomware
The Bad Rabbit ransomware spread across Eastern Europe in 2017, mimicking the modus operandi of the WannaCry attack but with a few tweaks.
Infected computers displayed a ransom note demanding Bitcoin. High-profile organizations, including airports and media outlets, found themselves at the mercy of this malicious software.
Malicious Browser Extensions
Cybercriminals have also crafted browser extensions designed to steal crypto-related information.
For instance, extensions masquerading as popular crypto wallet management tools have been discovered.
Once installed, they pilfered sensitive details, allowing the culprits to make unauthorized transactions.
Useful links
How to Remove Crypto Mining Malware

Discovering that your device has been compromised by crypto mining malware can be distressing.
However, it’s essential to approach its removal calmly and methodically.
Here’s a step-by-step guide on how to remove crypto mining malware.
Disconnect from the Internet
Begin by disconnecting your device from the internet. This action will prevent the malware from communicating with its server and potentially downloading additional malicious payloads.
Boot in Safe Mode
Before running any scans or removal tools, boot your computer in Safe Mode. This mode loads only essential drivers, preventing the malware from starting with your system. For Windows, you can access Safe Mode by pressing the F8 key during startup. For macOS, hold the Shift key during the boot process.
Use a Reputable Antivirus or Anti-Malware Program
Having a trusted security solution is crucial. Update your antivirus or anti-malware software to the latest definitions and run a thorough system scan. It should detect and quarantine the malicious files. Some recommended tools include Malwarebytes, Bitdefender, and AVG.
Manually Check Programs and Files
While your security software should catch most threats, it’s wise to manually check as well. Review the list of installed programs on your computer and uninstall any unfamiliar or suspicious software. Similarly, inspect system folders for any unusual files and remove them.
Clear Browser Cache and Extensions
Some cryptominers embed themselves within browsers. Clear your browser’s cache and cookies, and inspect your extensions or add-ons. Remove any that are unfamiliar or that you didn’t intentionally install.
Restore System
If you’re still experiencing issues or unsure about the malware’s complete removal, consider restoring your system to a previous state using system restore points. This action can roll back any changes made by the malware.
Regularly Update Software
Malware often exploits vulnerabilities in outdated software. Regularly updating your operating system and applications can help protect against these vulnerabilities.
Change Passwords
After ensuring the malware is removed, it’s a good idea to change passwords for important accounts. Although mining malware primarily focuses on using system resources, there’s no guarantee it hasn’t collected personal data.
Implement Preventive Measures
To avoid future infections, consider using ad blockers or anti-crypto mining browser extensions like No Coin. Moreover, avoid downloading files from untrusted sources, and always be wary of email attachments from unknown senders.
So, how to protect against crypto malware?
How to Protect Against Crypto Malware
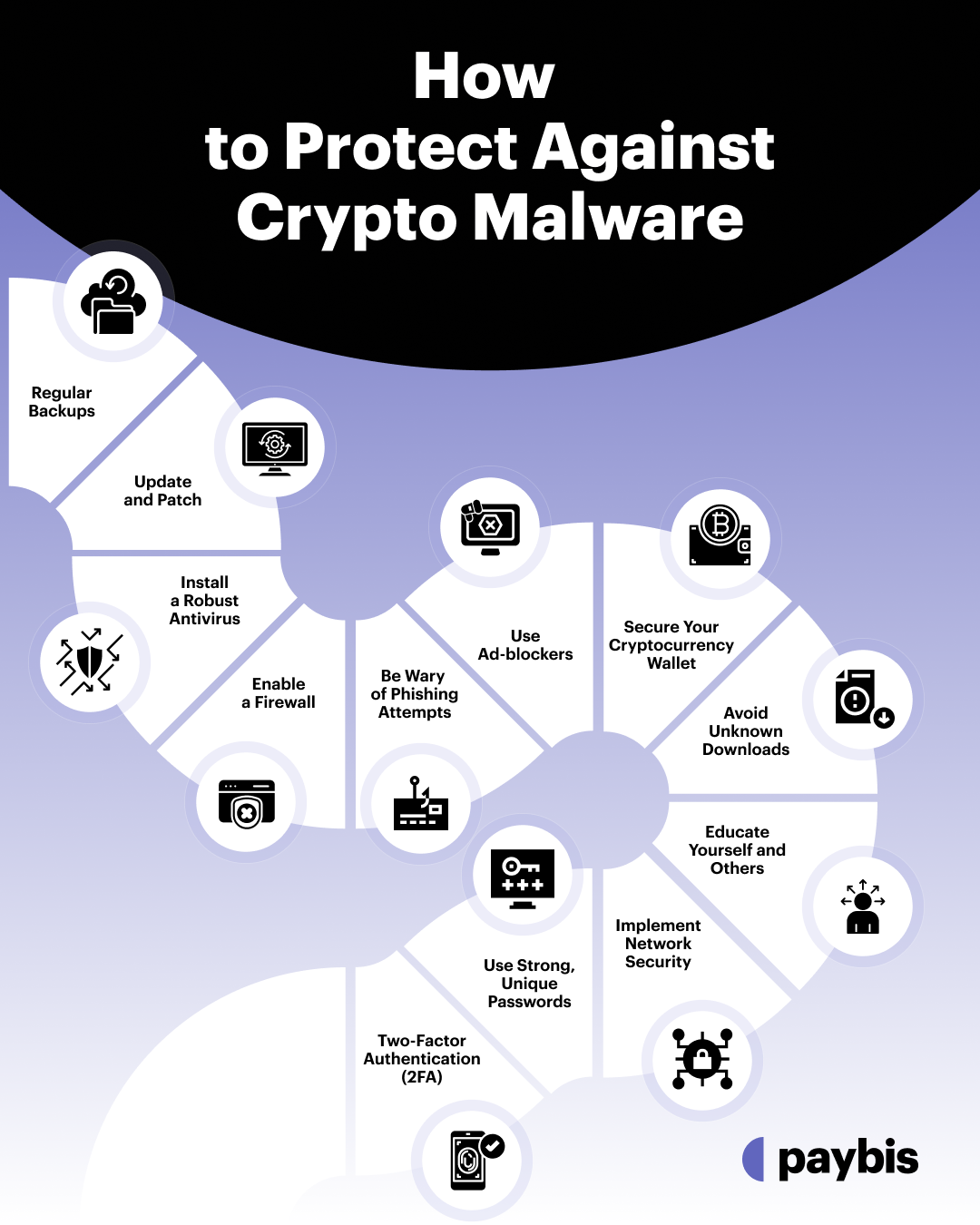
Protecting your devices and digital assets from crypto malware is more than just a reactionary measure; it’s about creating a robust defense system. Let’s discuss the various measures you can adopt to ensure your digital space remains safe and uncompromised.
Regular Backups
Make it a habit to back up your data regularly. In the unfortunate event of a ransomware attack, having backups ensures that you can restore your data without having to pay a ransom.
Update and Patch
Cybercriminals often exploit known vulnerabilities in software. By regularly updating your operating system and applications, you’re patching potential entry points.
Install a Robust Antivirus
Invest in a good antivirus or anti-malware software. Ensure it’s always up-to-date and set it to scan your device routinely.
Enable a Firewall
A firewall acts as the first line of defense against potential threats by blocking unauthorized access. Ensure it’s always active.
Be Wary of Phishing Attempts
Cybercriminals have become adept at crafting convincing fake emails. Avoid clicking on suspicious links or downloading attachments from unknown sources.
Use Ad-blockers
Malicious ads or malvertising can serve as conduits for cryptomalware. Consider using ad blockers to prevent such ads from displaying.
Secure Your Cryptocurrency Wallet
If you’re into cryptocurrencies, ensure your crypto wallet is secure. Here’s a guide on “Are Blockchain Wallets Safe” to help you in bolstering your wallet’s security.
Avoid Unknown Downloads
Only download software and apps from trusted sources. Unknown or pirated software can sometimes be bundled with crypto malware.
Educate Yourself and Others
Awareness is one of the most potent weapons against cyber threats. Familiarize yourself with the latest tactics and techniques used by cybercriminals.
Implement Network Security
If you run a business or manage multiple devices, implement network security solutions, including intrusion detection systems.
Use Strong, Unique Passwords
Ensure you use strong, unique passwords for all your accounts and change them periodically.
Two-Factor Authentication (2FA)
Wherever possible, enable 2FA for your online accounts. This adds an extra layer of security, ensuring that even if your password is compromised, unauthorized access is still prevented.
Cryptomalware Was Inevitable. Stay Safe with Paybis.
The cryptocurrency revolution, while a monumental stride towards decentralization and financial empowerment, has inadvertently ushered in a new breed of cyber threats: crypto malware.
This nefarious subset of malware preys on the uninformed, exploiting both software vulnerabilities and human psychology. As digital currencies continue to rise in popularity, so does the attractiveness of the crypto ecosystem for malicious actors.
From silently hijacking computing resources for mining to direct theft of digital assets, the modes of exploitation are varied and evolving.
For a deeper dive into the world of cryptocurrencies, their challenges, opportunities, and myriad ways to navigate this space safely, make sure to stay updated with the Paybis blog. Your next layer of knowledge and protection might just be a click away.
FAQ
How do I know if I have crypto malware?
Signs include ransom notes, encrypted files, decreased device performance, high CPU usage, and unexpected system behaviors. Regular scans with updated security software can detect most infections.
Why is crypto malware so successful?
Crypto malware exploits software vulnerabilities and preys on users’ emotions, leveraging panic and urgency to maximize impact and profit.
Can malware steal crypto?
Yes, specific malware can target cryptocurrency wallets, intercept transactions, or modify recipient addresses, leading to theft.
How do I get rid of mining malware?
Disconnect from the internet, use reputable antivirus and anti-malware tools to scan and eliminate the malware, and then update all software.
How does crypto mining malware work?
It covertly utilizes a device’s resources to mine cryptocurrency, operating silently in the background and sending mined coins to the attacker’s wallet.
Disclaimer: Don’t invest unless you’re prepared to lose all the money you invest. This is a high‑risk investment and you should not expect to be protected if something goes wrong. Take 2 mins to learn more at: https://go.payb.is/FCA-Info